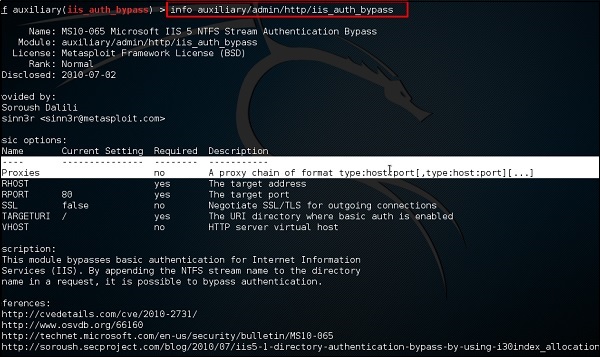
اشتري اونلاين بأفضل الاسعار بالسعودية - سوق الان امازون السعودية: AWS Penetration Testing: Beginner's guide to hacking AWS with tools such as Kali Linux, Metasploit, and Nmap : Helmus, Jonathan: كتب
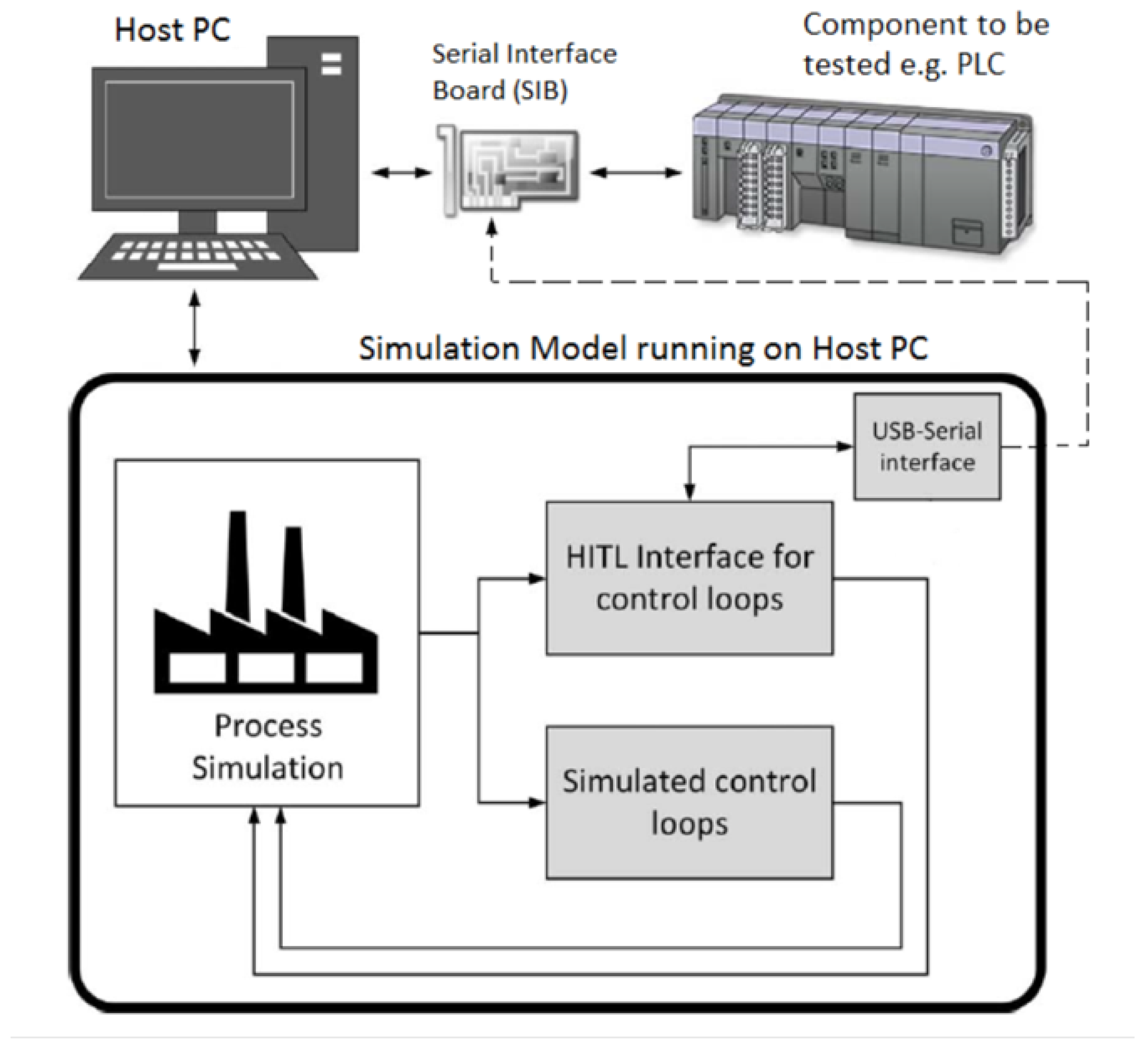
JSAN | Free Full-Text | Preliminaries of Orthogonal Layered Defence Using Functional and Assurance Controls in Industrial Control Systems

Exploit the Fuzz – Exploiting Vulnerabilities in 5G Core Networks | NCC Group Research Blog | Making the world safer and more secure

Hacking: The Underground Guide to Computer Hacking, Including Wireless Networks, Security, Windows, Kali Linux and Penetration Testing by Abraham K White - Ebook | Scribd

Writing Exploits for Win32 Systems from Scratch | NCC Group Research Blog | Making the world safer and more secure

AWS Penetration Testing: Beginner's guide to hacking AWS with tools such as Kali Linux, Metasploit, and Nmap eBook : Helmus, Jonathan: Amazon.com.au: Books