Methodology for acute lymphoblastic leukemia (ALL) image classification | Download Scientific Diagram

Algorithmic evaluation of the proposed work (MFSLnO) for positive and... | Download Scientific Diagram
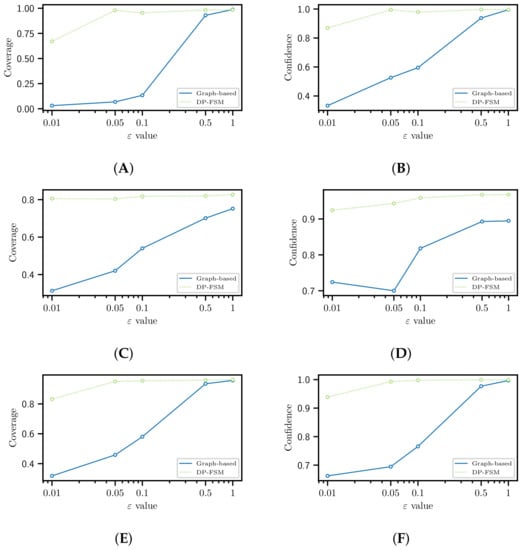
Applied Sciences | Free Full-Text | A Graph-Based Differentially Private Algorithm for Mining Frequent Sequential Patterns

Sources of percent correct and percent error in the validation for 13... | Download Scientific Diagram
ICT-32-2014: Cybersecurity, Trustworthy ICT WITDOM “empoWering prIvacy and securiTy in non-trusteD envirOnMents” D3.5 – WI
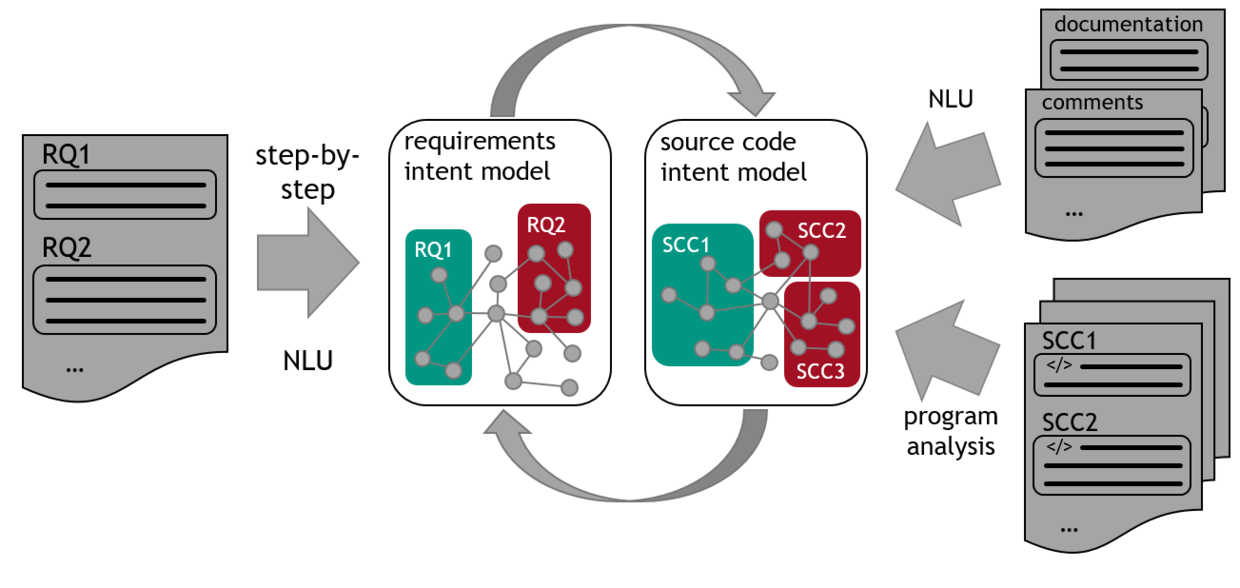
KIT - IPD Tichy - Core competences - Projects - INDIRECT: Intent-driven Requirements-to-Code Traceability

Recognizing Fake identities in Online Social Networks based on a Finite Automaton approach | Semantic Scholar

Secure clustering for efficient data dissemination in vehicular cyber-physical systems | Semantic Scholar
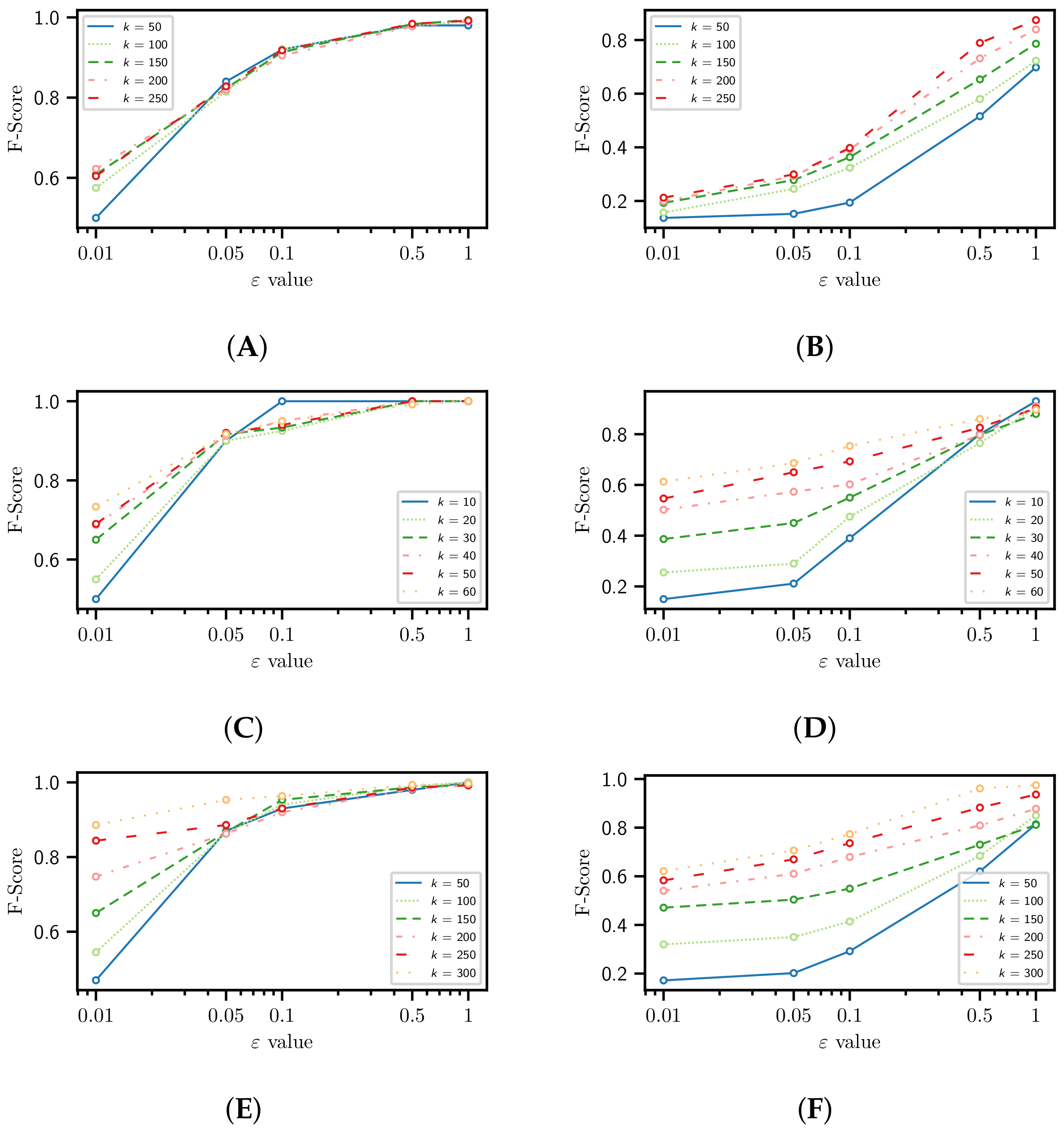
Applied Sciences | Free Full-Text | A Graph-Based Differentially Private Algorithm for Mining Frequent Sequential Patterns
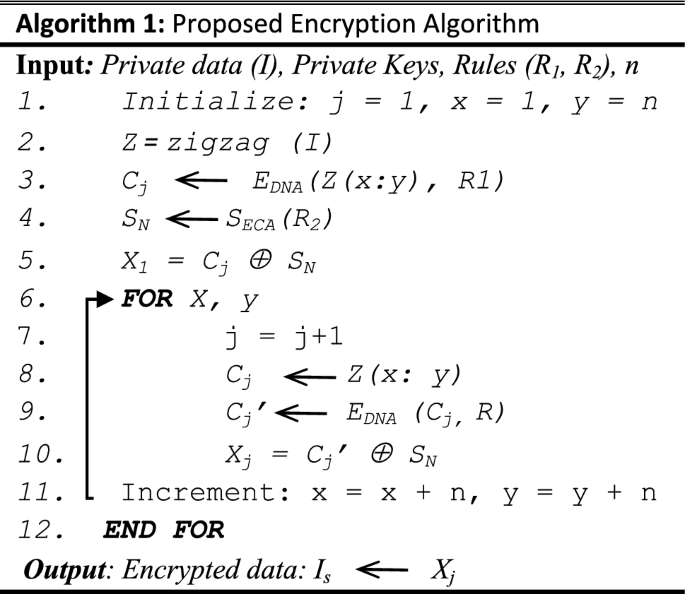
CADEN: cellular automata and DNA based secure framework for privacy preserving in IoT based healthcare | SpringerLink

Application layer classification of Internet traffic using ensemble learning models - Arfeen - 2021 - International Journal of Network Management - Wiley Online Library

PDF) Proceedings Fourth International Symposium on Games, Automata, Logics and Formal Verification | Tiziano Villa - Academia.edu

Agent-based modelling to simulate farmers' sustainable decisions: Farmers' interaction and resulting green consciousness evolution - ScienceDirect